Since the beginning of the Web age, crooks have searched for approaches to benefit on clueless individuals while they peruse the Internet. Infections, malware, and different plans were created to contaminate and penetrate frameworks, both at the endeavor and shopper levels. One of the best types of cybercrime is social designing, otherwise called the cheat of the Web.
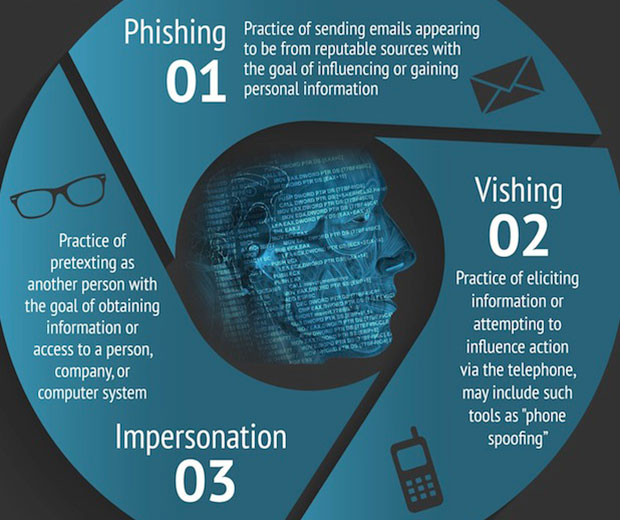
Social building really covers a wide scope of security dangers, those in an advanced setting, however, it's typically connected with assaults like phishing, where the criminal is attempting to take data from a client. Realizing how to safeguard yourself from such dangers is basic to guarding your online information.
Here's a gander at how social designing methods have developed after some time and what individuals and organizations need to do later on to secure themselves.
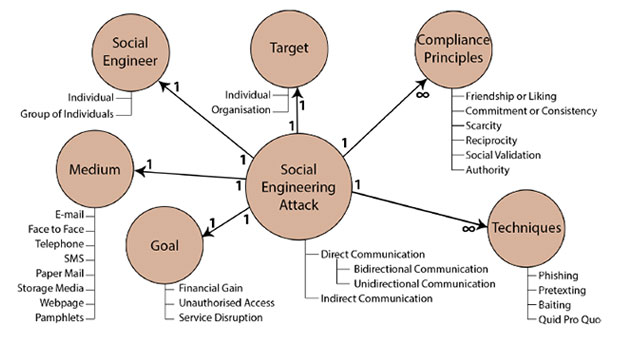
Components of an Assault
The establishment of any social designing assault is trust. The criminal is looking to pick up your trust through loathsome strategies so as to get something, which could incorporate access consents, passwords, or physical access to a structure or a bit of equipment.
Much of the time, social building assaults are completed via telephone or on the web, with the goal that hoodlums can camouflage their actual personalities.
For instance, you may have caught wind of tricks where individuals get different telephone calls at home about a security issue with the Windows working framework. The assailant attempts to increase enough trust to persuade the objective to give a Mastercard number via telephone.
Online social building is increasingly basic in light of the fact that it is so natural to perform in mass. The best model is a broad phishing trick. A programmer conveys a lot of messages that attempt to mirror the look and feel of a bank or other organization. The objective is to have Web clients click on maverick connections and enter passwords or other touchy data on a mock page.
New Types of Social Designing
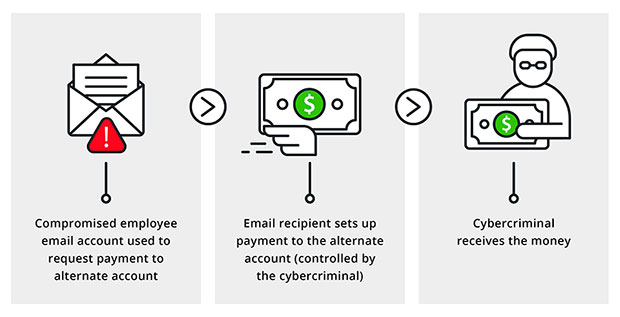
Cybercriminals realize that even the best tricks will come up short on steam in the long run, which is actually why they are continually exploring different avenues regarding new types of social building. One developing pattern is the business email bargain (BEC). Aggressors use telephone and email messages together to mimic a corporate official and start false cash moves.
People likewise should be watchful for blackmail tricks. In case you're a casualty of this sort of assault, you'll get a message asserting that the sender has implicating proof about something you did previously. These assaults regularly are focused on and will utilize genuine names and occupation narratives.
In conclusion, there's catphishing which is a mix of an email phishing trick and a catfishing faker. The aggressor typically will profess to be a family member or admirer of an individual inside an association and persuade representatives to give touchy data.
Preparing a Cutting edge Workforce
Social building assaults are particularly perilous in light of the fact that everything necessary is one powerless connection in an association to start a harming occasion. For instance, if a server overseer succumbs to a phishing trick, that could leave an incredible secret phrase in the hands of a programmer, who at that point could execute a scope of assaults over the system.
One misstep that a ton of organizations make is to accept they should center their cybersecurity endeavors and spending plan on items like firewalls and interruption identification frameworks. While these are without a doubt important, you can't overlook that the most defenseless resources in your association are the individuals working in it.
Cybersecurity mindfulness preparing ought to be a key piece of your organization's onboarding procedure. Moreover, intermittent obligatory sessions ought to be held each quarter with an accentuation on social building to guarantee that your representatives comprehend what to look for and how to secure themselves.
One piece of the association that individuals frequently disregard is the remote workforce. There's an observation that on the off chance that they are situated outside of the system, their potential for harm is insignificant.
The inverse is in reality evident. Despite the fact that the best virtual private systems (VPNs) can secure you against programmers while you're working remotely, they won't square social building assaults. Therefore, remote and voyaging laborers ought to be additional careful when communicating with individuals over email or by telephone.
Looking Forward
Organizations need to stay careful with regards to cybersecurity, since social designing is just going to get increasingly refined later on. It won't be long until crooks start utilizing man-made reasoning and AI calculations to their advantage.
For instance, a chatbot program could be utilized to impersonate the composing style of a human in a live phishing situation. Since it would be completely machine-based, programmers would have the option to execute this kind of social designing assault on a more extensive scale than any time in recent memory.
Or on the other hand think about the headways in voice reenactment, which presently takes into account computerized aides to speak with a client with no language obstructions. This will make it simpler for cybercriminals to mimic various people and influence those associations for their advantage.
Last Considerations
Most cybersecurity procedures are intended to deal with direct situations. Firewall frameworks are worked to get a lot of rules and afterward channel Web traffic dependent on those guidelines. The equivalent is valid for malware scanners, which check portions of a working framework and search for hazardous code.
Where it gets extremely precarious is with assaults like social building, which present a human component that is difficult to foresee or control. No one can really tell how a representative will respond when focused in a phishing or coercion trick. Indeed, even the best preparing projects won't have the option to look forward to new types of cyberattacks.
What's significant is that each endeavor recall that supporting cybersecurity must be a progressing action. You can't just toss cash at it with a lot of devices and trainings and expect your frameworks will be protected pushing ahead. Associations need to keep awake to date with best practices and ensure their workers do as well.






0 Comments